Simple AAA lab
I decide to start with identity management part of the blueprint. I have few good reasons for that
1) We are implementing complex AAA solution in my current job (3 ACSs, accounting, assigning privilege levels to users, RSA authentication etc…)
2) Its not most difficult area – so its good for slow start
3) Those topics (AAA, 802.1x, NAC are heavily covered in the written exam)
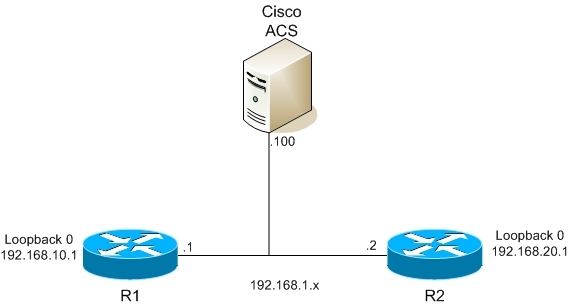
As a first part I created simple topology with two routers and one Cisco ACS (you can get it from Cisco they offers 90 day trial – click here (you need CCO account for it)).
So with this easy lab you can practice all AAA and ACS features (privilege levels, command authorization, accounting on ACS etc..)…Its really simple lab, you need just two routers and one server… it can be also easily done with dynamips… Its really easy lab and its more for CCSP (or even for CCNA) – its more pre-configuration (in next parts I will try to dig deeper)
One router is used for radius (R1) second is used for tacacs+ (R2)
STEPS
1. Basic IP addressing
(loopback int will be used as source for AAA communication on ACS)
R1
interface fa 0/0
ip address 192.168.1.1 255.255.255.0
no shut
interface loopback0
ip address 192.168.10.1 255.255.255.0
R2
interface fa 0/0
ip address 192.168.1.2 255.255.255.0
no shut
interface loopback0
ip address 192.168.20.1 255.255.255.0
2. Set communication between ACS and radius/tacacs+ routers
R1
aaa new-model
tacacs-server host 192.168.1.100
tacacs-server key ciscolab
ip tacacs source-interface loopback 0
R2
aaa new-model
radius-server host 192.168.1.100
radius-server key ciscolab
ip radius source-interface loopback 0
3. Add device to ACS and create ACS users
For R1 – on ACS select Network configuration and Add AAA client – enter AAA client hostname R1 , AAA client IP address 192.168.10.1 (remember we created ip radius source loopback0) and key is ciscolab, protocol is RADIUS (IETF) same for R2, IP is 192.168.20.1 and protocol is TACACS+
For users creation on ACS click on USER SETUP and fill in username/password … I created two users user1 and user2 with password cisco..
That is we have basic setup ..
You can test AAA from router with test aaa command
R1#test aaa group radius user1 cisco legacy
Attempting authentication test to server-group radius using radius
User was successfully authenticated.
Same for TACACS+
R1#test aaa group tacacs user1 cisco legacy
Attempting authentication test to server-group tacacs+ using tacacs+
User was successfully authenticated.
Following the blueprint
As has been already written several times in the LAB you can expect ANYTHING from the Blueprint… So i decide to organize all my study notes according this blueprint … there is 6 major topics
- Firewall
- VPN
- Intrusion Prevention System (IPS)
- Identity Management
- Advanced Security
- Network Attacks
My firefox bookmarks for CCIE are organized exactly in this style and order.. If I see some interesting config guide, tutorial etc. related to CCIE security I bookmark the page and place to the proper folder. |
Structure of my mailbox what I use for newsgroups like groupstudy or OSL is exactly same six folders (plus lot of subfolders)… So if need get some information (ideas for lab) i just open my bookmarks or my email folder….
If you look to the right topics for blog entries have same structure as well (maybe some topics are missing because there are no posts but I hope soon we will have complete blueprint)



1 comment