Reset ACS to its default configuration
When you finish you labs on router, pix or switch you erase configuration to be able re-doing lab or to start a new lab… But what about ACS if you add device, create users, groups… how to remove it, how to have default ACS settings???… There is nothing like write erase command so I use following easy trick…
When I install new ACS my first step is backup this fresh configuration
System configuration —>ACS Backup
 s
s
Backup files are stored in the folder
C:\Program Files\CiscoSecure ACS v4.0\CSAuth\System Backups
File is named by default with format day-month-year time.dmp but you can manually rename it to whatever you want (as i did to defaultACS.dmp)
Than you can restore configuration anytime with
System configuration —>ACS restore
and just select your backup file and click on restore
Simple AAA lab
I decide to start with identity management part of the blueprint. I have few good reasons for that
1) We are implementing complex AAA solution in my current job (3 ACSs, accounting, assigning privilege levels to users, RSA authentication etc…)
2) Its not most difficult area – so its good for slow start
3) Those topics (AAA, 802.1x, NAC are heavily covered in the written exam)
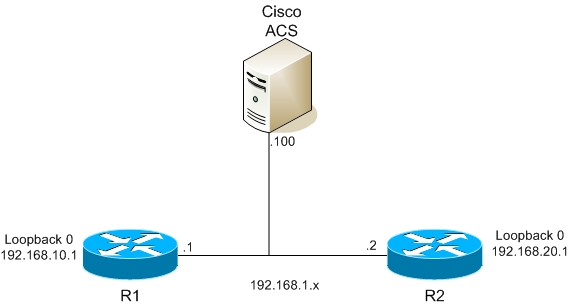
As a first part I created simple topology with two routers and one Cisco ACS (you can get it from Cisco they offers 90 day trial – click here (you need CCO account for it)).
So with this easy lab you can practice all AAA and ACS features (privilege levels, command authorization, accounting on ACS etc..)…Its really simple lab, you need just two routers and one server… it can be also easily done with dynamips… Its really easy lab and its more for CCSP (or even for CCNA) – its more pre-configuration (in next parts I will try to dig deeper)
One router is used for radius (R1) second is used for tacacs+ (R2)
STEPS
1. Basic IP addressing
(loopback int will be used as source for AAA communication on ACS)
R1
interface fa 0/0
ip address 192.168.1.1 255.255.255.0
no shut
interface loopback0
ip address 192.168.10.1 255.255.255.0
R2
interface fa 0/0
ip address 192.168.1.2 255.255.255.0
no shut
interface loopback0
ip address 192.168.20.1 255.255.255.0
2. Set communication between ACS and radius/tacacs+ routers
R1
aaa new-model
tacacs-server host 192.168.1.100
tacacs-server key ciscolab
ip tacacs source-interface loopback 0
R2
aaa new-model
radius-server host 192.168.1.100
radius-server key ciscolab
ip radius source-interface loopback 0
3. Add device to ACS and create ACS users
For R1 – on ACS select Network configuration and Add AAA client – enter AAA client hostname R1 , AAA client IP address 192.168.10.1 (remember we created ip radius source loopback0) and key is ciscolab, protocol is RADIUS (IETF) same for R2, IP is 192.168.20.1 and protocol is TACACS+
For users creation on ACS click on USER SETUP and fill in username/password … I created two users user1 and user2 with password cisco..
That is we have basic setup ..
You can test AAA from router with test aaa command
R1#test aaa group radius user1 cisco legacy
Attempting authentication test to server-group radius using radius
User was successfully authenticated.
Same for TACACS+
R1#test aaa group tacacs user1 cisco legacy
Attempting authentication test to server-group tacacs+ using tacacs+
User was successfully authenticated.
Following the blueprint
As has been already written several times in the LAB you can expect ANYTHING from the Blueprint… So i decide to organize all my study notes according this blueprint … there is 6 major topics
- Firewall
- VPN
- Intrusion Prevention System (IPS)
- Identity Management
- Advanced Security
- Network Attacks
My firefox bookmarks for CCIE are organized exactly in this style and order.. If I see some interesting config guide, tutorial etc. related to CCIE security I bookmark the page and place to the proper folder. |
Structure of my mailbox what I use for newsgroups like groupstudy or OSL is exactly same six folders (plus lot of subfolders)… So if need get some information (ideas for lab) i just open my bookmarks or my email folder….
If you look to the right topics for blog entries have same structure as well (maybe some topics are missing because there are no posts but I hope soon we will have complete blueprint)
Routing, switching and frame-relay for CCIE security LAB
Maybe (as CCIE security candidate) you are wondering how deep do you need master routing, switching and FR topics. This topics are core for R&S lab but we need quite deep knowledge as well. Before version 2 CCIE security lab was more like CCIE R&S with security features , plus some security device…in version 2 is switching, routing and frame relay pre-configured but it, of course, doesn’t mean we don’t need to know those technologies
What CISCO says ?????
I found following information on Cisco networkers CCIE Security Techtorial – I guess this is from 2006 but its for version 2
The Routers and Switches in Your Topology Are Preconfigured With:
• Basic IP addressing, hostname, passwords
• Switching: Trunking, VTP, VLANs
• Frame Relay: DLCI mapping (static/dynamic)
• Core Routing: OSPF, RIP, EIGRP, BGP
• All pre-configured passwords are ‘cisco’
Security Devices (PIX,ASA,VPN3000, IDS) Are Not Initialized. Candidate Is Required to Do So
I found interesting post on Cisco Netpro (question answered by Yusuf Cisco CCIE security program manager)
“IP routing, basic Layer 2 (basic switching, FR) will be pre-configured on Routers and Switches only. You still have to do some configs on the security appliances (PIX/ASA, IPS, VPN3k). In some occasions, you may also have to do some additional Layer2/3 configs to complete a task. Some questions in the exam relate to troubleshooting skills, which will require you to identify errors in the preloaded configs. These errors could be of any part of your network… It will be a network-wide troubleshooting.”
So it means we need to able identify VLAN misconfiguration , Routing protocols misconfiguration, DLCI number misconfiguration etc….
Lets look to all technologies
SWITCHING
Easiest part for me (and I guess for everyone)… I am quite confident in switching part ( I worked on LANs with more than 1800 PCs so STP, VTP, ether channel, trunks, )
According mentioned Security Techtorial:
following switching features are pre-configured VTP domain, VLAN database, Port-VLAN assignment
No big suprise everyone who practice labs at home or rents labs from a vendor starts with this pre-configuration
We are required to configure catalyst security features like Port Security, 802.1x, AAA, Traffic Control, SPAN, RSPAN so I believe who wants to master this features is familiar with switching fundamentals like spanning tree or VTP
ROUTING
This is more difficult than switching… I don’t mean more difficult as technology (its of course) but more difficult how to determine what skills are needed … Well core routing is pre-configured on routers, but we still need to configure all the routing on ASA firewalls….
But we can be asked to allow RIP, OSPF, EIGRP or BGP THROUGH firewall so we need to know protocol architecture (ports used, multicast IP etc ..)
If we look on routing configuring on firewalls so ASA 7.x supports RIP, OSPF there is no support for BGP and EIGRP comes in version 8.0(2) So it means we need to be really, really familiar what OSPF and RIP features
OSPF on ASA is more IOS like… The security appliance supports the following OSPF features:
•Support of intra-area, inter area, and external (Type I and Type II) routes.
•Support of a virtual link.
•Authentication to OSPF packets (both password and MD5 authentication).
•Support for configuring the security appliance as a designated router or a designated backup router. The security appliance also can be set up as an ABR; however, the ability to configure the security appliance as an ASBR is limited to default information only (for example, injecting a default route).
•Support for stub areas and not-so-stubby-areas.
•Area boundary router type-3 LSA filtering.
•Advertisement of static and global address translations.
Redistribution is supported on ASA you can redistribute routes into an OSPF routing process from another OSPF routing process, a RIP routing process, or from static and connected routes configured on OSPF-enabled interfaces
So if this ASA supports we need to master it – even some features (like ABR) are probably not used in real world scenarios – but it is still CCIE lab so we can expect it … Of course we are not supposed to know every detail as our colleagues from R&S track and I think most of those topics are covered in CCNP material. I think good CCNP knowledge with some routing experience should be enough for routing part of CCIE security
RIP on ASA is much more easier than OSPF – you can enable only one RIP routing process at same time, you can select passive or default mode …..
Don’t forget we are still required to configure routing protocols security features like is AUTHENTICATION (clear text, MD5)..
Of course we are not supposed to know every detail as our colleagues from R&S track and I think most of those topics are covered in CCNP material. I think good CCNP knowledge with some routing experience should be enough for routing part of CCIE security
FRAME-RELAY
Next is FR – according Cisco DLCI are pre-configure as well as FRSW (we dont even have access to frame-relay switch)… I think we should be familiar what FR can be used (spoke, hub and spoke, point-to-pint subinterfaces etc….)
As has been already said, if you practice for the LAB in your home lab or you rent remote labs as first step you need configure L2 stuff… I have never worked in ISP environment so at the beginning my knowledge of the technology was very limited but there is lot of good materials on Cisco website and on Internet
To get familiar with FR topologies you can use free chapters from book Cisco FR Configurations . Also on Cisco website you can find lot of FR examples
NO PAIN, NO GAIN
If I am lacking motivation for my CCIE study I always watch following KILL BILL II. movie scene with PEI MEI
Do you think is there any relation between that scene and CCIE (or other) study??? I think yes – Uma Thurman wants master kung-fu as I want master networking knowledge. She needs to work very, very hard to get to the top level as I need to work very, very hard to get my CCIE.
During her “bootcamp” :))) with PEI MEI she suffers a lot but thanks this she gets excellent kung-fu skills (and later it will save her life). You probably know great poverb NO PAIN, NO GAIN and its true if you want to get to an expert level (and It doesnt matter if its football, dancing, surgery ot networking). Some people are talented but they still need work hard to get expert level… I dont think Iam extra talented for networking so need to work much more harder…but back to the movie
I love the dialogue when Uma first time comes to PEI MEI… So I changed little bit that dialogue .. Imagine CCIE candidate is Uma and CCIE proctor is PEI MEI
(NOTE: I know CCIE proctors are very nice persons – but in following conversation CCIE proctor represents difficulty of the exam)
Proctor: Your master told me you’re not entirely unschooled. What training do you possess?
CCIE candidate: I am proficient in DMVPN. And I am more than proficient in firewalling
Proctor: Don’t make me laugh. Your anger amuses me. Do you believe you are my match?
CCIE candidate: No.
Proctor:Is it your wish to fail the lab?
CCIE candidate: No.
Proctor: You breathe hard. Is there anything you do well? — Oh yes, you know firewalling. Go to that rack.
Proctor: Plug the console cable… Let’s see how good you really are. Configure firewall ASA to allow BGP traffic with NAT
Proctor: Your ability really is quite poor.
Proctor: Give up? Or care to try again? Your configuration skill is amateur at best
Proctor: I asked you to show me what you know, and you did. Not a goddamn thing.
…
….
It always helps me to realize that only hard work leads to the success, there are no shortcuts….. I have just started my CCIE security preparation but i know i need to sacrifice my personal and social life..
Welcome to this blog
This blog should describe my road to CCIE in security. I would like to share my ideas and study notes as well as track my study progress.. I hope there will be post with 5 digits in the heading
If you are intersted you can read something about me and you can reach me on denyip at linuxmail.org




leave a comment