Using AUTOCOMMANDs
I tested autocommand feature (command run automatically when user is logged in) and it looks authorization is needed in order get this features working
without commad aaa authorization exec default local it didn’t work for me (if you have other experience let us know)
So configuration is following ( I tested it with show ip interface brief command)
aaa new-model
aaa authentication login default local
aaa authorization exec default local
username user1 password 0 cisco
username user1 autocommand show version
When user1 logs in
R2#telnet 192.168.1.1
Trying 192.168.1.1 … Open
User Access Verification
Username: user1
Password:
R1>sh ip int brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/1 192.168.1.1 YES NVRAM up up
Loopback0 192.168.10.1 YES NVRAM up up
[Connection to 150.50.78.2 closed by foreign host]
When using NOHANGUP feature with command
username user1 nohangup autocommand show version
it doesn’t mean you will stay logged in (as I though) but you get new user login prompt(instead of [Connection to 150.50.78.2 closed by foreign host] message)
R2#telnet 192.168.1.1
Trying 192.168.1.1 … Open
User Access Verification
Username: user1
Password:
R1>sh ip int brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/1 192.168.1.1 YES NVRAM up up
Loopback0 192.168.10.1 YES NVRAM up up
User Access Verification
Username:
So if you have credentials only for user1 – this autocommand is only one thing you can do
Multiple TACACS+ servers with different keys
Have you ever tried to add more than one TACACS+ server??? When I tried I was forced to use same authentication key for them (it could be possible security issue)
tacacs-server host 192.168.1.100
tacacs-server host 192.168.1.101
tacacs-server key secretkey
Its difference from RADIUS command where you can specify key after IP address
radius-server host 192.168.1.100 key secretkey1
radius-server host 192.168.1.101 key secretkey2
Now I found workaround how to do same for TACACS+ it can be done with server-private command under aaa group server
NOTE this command was introduced to IOS 12.3(7)T so it doesn’t apply to current blueprint version
aaa group server tacacs+ my-servers
server-private 192.168.1.100 key secretkey1
server-private 192.168.1.100 key secretkey2
Reset ACS to its default configuration
When you finish you labs on router, pix or switch you erase configuration to be able re-doing lab or to start a new lab… But what about ACS if you add device, create users, groups… how to remove it, how to have default ACS settings???… There is nothing like write erase command so I use following easy trick…
When I install new ACS my first step is backup this fresh configuration
System configuration —>ACS Backup
 s
s
Backup files are stored in the folder
C:\Program Files\CiscoSecure ACS v4.0\CSAuth\System Backups
File is named by default with format day-month-year time.dmp but you can manually rename it to whatever you want (as i did to defaultACS.dmp)
Than you can restore configuration anytime with
System configuration —>ACS restore
and just select your backup file and click on restore
Simple AAA lab
I decide to start with identity management part of the blueprint. I have few good reasons for that
1) We are implementing complex AAA solution in my current job (3 ACSs, accounting, assigning privilege levels to users, RSA authentication etc…)
2) Its not most difficult area – so its good for slow start
3) Those topics (AAA, 802.1x, NAC are heavily covered in the written exam)
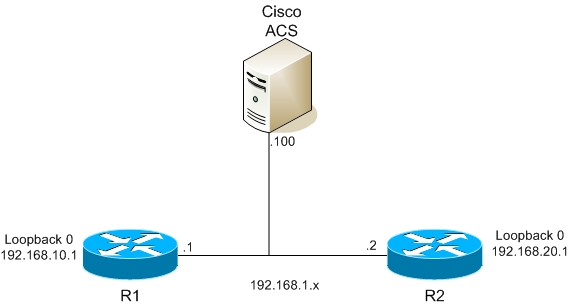
As a first part I created simple topology with two routers and one Cisco ACS (you can get it from Cisco they offers 90 day trial – click here (you need CCO account for it)).
So with this easy lab you can practice all AAA and ACS features (privilege levels, command authorization, accounting on ACS etc..)…Its really simple lab, you need just two routers and one server… it can be also easily done with dynamips… Its really easy lab and its more for CCSP (or even for CCNA) – its more pre-configuration (in next parts I will try to dig deeper)
One router is used for radius (R1) second is used for tacacs+ (R2)
STEPS
1. Basic IP addressing
(loopback int will be used as source for AAA communication on ACS)
R1
interface fa 0/0
ip address 192.168.1.1 255.255.255.0
no shut
interface loopback0
ip address 192.168.10.1 255.255.255.0
R2
interface fa 0/0
ip address 192.168.1.2 255.255.255.0
no shut
interface loopback0
ip address 192.168.20.1 255.255.255.0
2. Set communication between ACS and radius/tacacs+ routers
R1
aaa new-model
tacacs-server host 192.168.1.100
tacacs-server key ciscolab
ip tacacs source-interface loopback 0
R2
aaa new-model
radius-server host 192.168.1.100
radius-server key ciscolab
ip radius source-interface loopback 0
3. Add device to ACS and create ACS users
For R1 – on ACS select Network configuration and Add AAA client – enter AAA client hostname R1 , AAA client IP address 192.168.10.1 (remember we created ip radius source loopback0) and key is ciscolab, protocol is RADIUS (IETF) same for R2, IP is 192.168.20.1 and protocol is TACACS+
For users creation on ACS click on USER SETUP and fill in username/password … I created two users user1 and user2 with password cisco..
That is we have basic setup ..
You can test AAA from router with test aaa command
R1#test aaa group radius user1 cisco legacy
Attempting authentication test to server-group radius using radius
User was successfully authenticated.
Same for TACACS+
R1#test aaa group tacacs user1 cisco legacy
Attempting authentication test to server-group tacacs+ using tacacs+
User was successfully authenticated.




1 comment